The IT and Security Recap of WWDC 2023
WWDC23 is over, and as always, it gave us a grab-bag of news to pore over and debate. Unsurprisingly, most of the coverage of WWDC focused on the big reveals in the keynote address and state of the union.
In particular, there has been a huge, polarized reaction to the Vision Pro, which will either revolutionize life as we know it or become an embarrassing footnote in Apple’s history. (I’m not going to try and predict which will happen since I laughed at the Apple Watch when it came out, and now you’ll never see me without one on my wrist.)
If you’re an IT or security professional, you may have looked at the WWDC coverage and concluded that there wasn’t much in it for you. But that’s where you’d be wrong–WWDC had a lot of stories that will impact your work life; you just have to know where to look.
You can start with in-depth coverage from the event, such as John Gruber’s The Talk Show Live (and check out their presenting sponsor, which seems like a super cool company).
But you’ll find the most comprehensive guide to the changes coming to enterprise Mac management in the developer sessions.
You likely don’t have time to listen to them all, so we’re going to summarize and provide analysis of a few key sessions:
- What’s new in managing Apple devices
- Explore advances in declarative device management
- Deploy passkeys at work
- Network Relays
- Meet device management for Apple Watch
This list doesn’t cover everything, but it does let us touch on the major trends we saw this year.
There’s a definite narrative in WWDC 2023’s IT updates: Apple is at a moment of transition in terms of how it fits into the enterprise.
There’s a tension apparent between Apple’s dedication to user agency and privacy and its need to give admins more control. Likewise, Apple is trying to work in harmony with existing tools like MDMs and VPNs while simultaneously building features designed to replace them.
In short: there’s a lot going on here that has nothing to do with face computers.
What’s new in managing Apple devices: WWDC 2023
This session provides a general rundown of topics that get more attention elsewhere (such as watchOS), but it also goes deep on a few areas.
Changes to device enrollment: macOS 14 gives IT more control over automated device enrollment, such as ensuring that FileVault is turned on and requiring a specific OS version before the user logs in for the first time.
More granular user restrictions: Instead of graying out entire sections of System Settings, admins can now give users permissions on a case-by-case basis. We’ll quote the transcript here: “In macOS 14, new restrictions prevent users from modifying Apple ID logins and Internet Accounts, adding local user accounts, and many more, like preventing Time Machine Backups.” You can also use Authorization Groups to write policies, such as giving standard (non-admin) users the ability to modify printer configurations. That alone should be enough to make IT teams jump for joy.
Introducing Managed Device Attestation for macOS: This capability–which was originally for iOS–reports on the device’s identity as well as device properties such as SIP status, secure boot status, OS version, whether third-party kernel extensions are allowed, and more. We can view this as a step towards first-party device trust, but it’s still a relatively short list of device properties (at least compared tothe visibility you get with OSquery).
Expanding platform Single Sign-On: This recently-introduced feature now allows users to create a local account during login using their SSO credentials, which is great for shared devices.
Updates to password compliance management: Obviously, Apple wants everyone to transition away from passwords and onto passkeys. But in the meantime, they’re updating compliance enforcement by taking some inspiration from nudge tools. Now, if a user’s password isn’t compliant, macOS will nag them with notifications every time they log in. Given the dubious efficacy of this tactic when it comes to getting users to install updates, we’ll see if this helps.
Declarative Device Management
Apple started talking about declarative device management (DDM) at WWDC21, where they said it “allows the device to be autonomous and proactive, freeing up the server to be lightweight…An autonomous device reacts to its own state changes and then applies management logic to itself without prompting from the server.”
In this session, they announced that declarative device management would both “provide more parity with MDM and help with transitioning from MDM.” The message to existing MDMs seems to be to adapt to this new paradigm or get left behind.
DDM has some profound implications for the future of Apple device management–check out Ryan Faas’ column for Computerworld for some more context–but for now, we’re going to focus on the update with the most immediate real world impact.
Enforcing software updates: Mac patch management has long been one of IT’s most frustrating and intractable problems since installing updates via forced restarts is so disruptive. macOS 14 tries to get users to install updates themselves by sending them notifications that get progressively more frequent as the deadline approaches. (There’s the influence of nudge tools again).
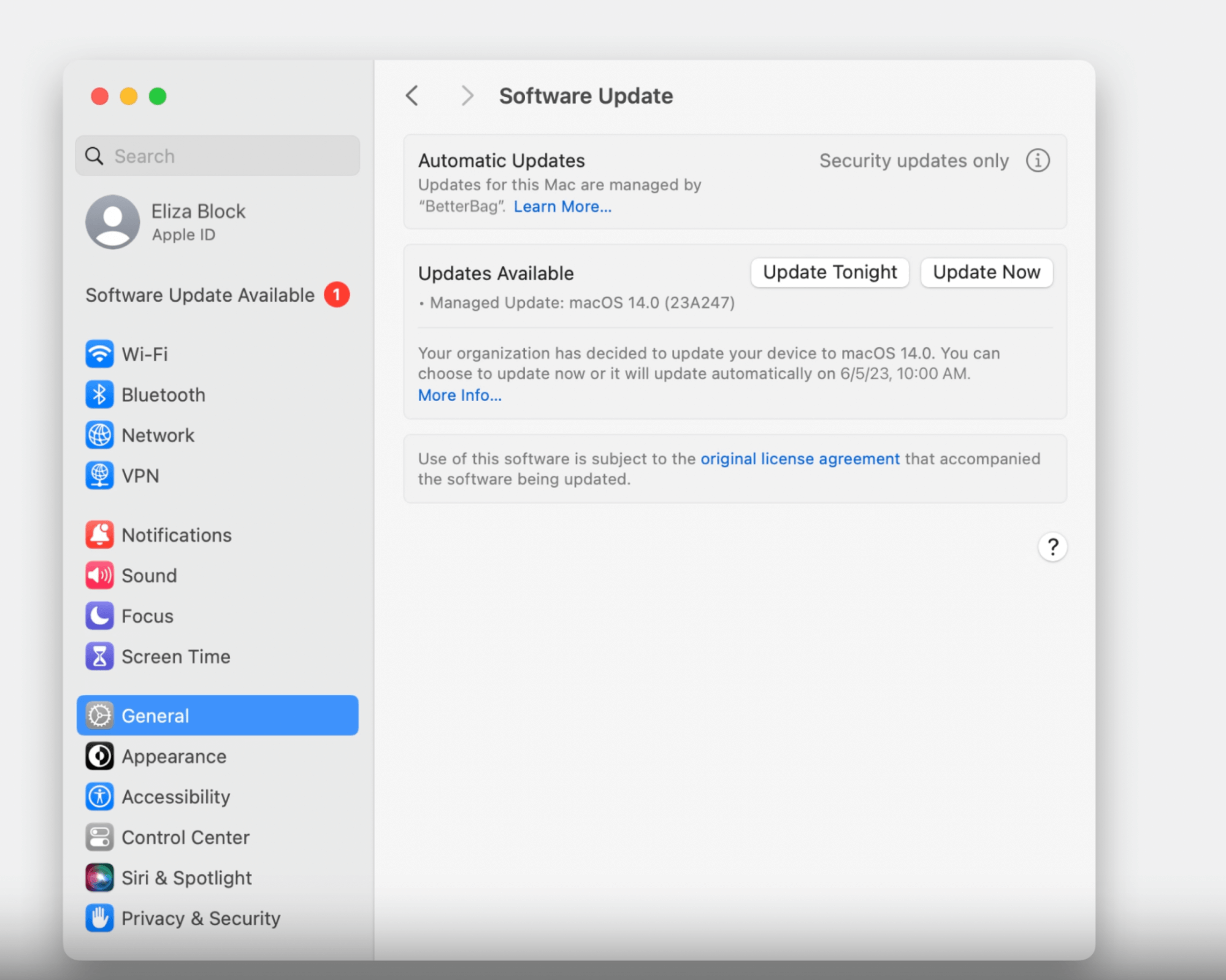
But once the deadline arrives, it looks like we’re back to automated updates via a forced restart. It remains to be seen whether the warning periods will be enough to get users to comply or if this method of patch management will remain so disruptive to end users.
So, Can You Deploy Passkeys at Work?
Passkeys have been available for a while, but until now, they’ve had only consumer-facing applications. But it looks like that’s about to change.
The first half of this session was an elaborate pitch for passkeys’ security and UI advantages. But anyone who’s been paying attention should already be sold on passkeys; we just want to know how to put them to use.
Here’s the rundown:
Implementing passkeys requires linking them to a user’s Managed Apple ID. There’s a separate session on Managed Apple IDs which is also worth checking out.
Using Managed Apple IDs disables passkey sharing, which makes sense in a corporate environment, even though Apple excitedly promoted passkey sharing for personal Apple IDs.
IT admins can choose what devices employees can use with their Managed Apple IDs: “…on any device, which is the default option, on managed devices only, which provides higher security and works for cases where users bring their own devices to work, or on managed supervised devices only, which is the highest level of security for organizations that provide devices to their employees.”
Network Relays Take a Bite Out of VPNs
WWDC’s “Ready, set, relay” session was one of those under-the-radar presentations that could wind up being among the most important for IT professionals. (It’s also one of the most technical, so we’re going to stick to the layman’s version.)
According to Apple, network relays have both customer and employee-facing applications. Developers can build them into their apps to bolster privacy, for example, “sensitive information about users…you may want to ensure that your own servers can’t associate that information with client IP addresses.
The more relevant use case for IT is employing network relays as a VPN alternative. They claim that "a relay provides a better user experience, is more performant, and is easier to manage than a VPN.” They go on that “since you can configure multiple relays simultaneously, it is easier to access different private domains in different networks.”
This development could be seen as another nail in the coffin for the beleaguered enterprise VPN market, but elsewhere, Apple emphasizes its compatibility with VPNs. In fact, one of the major updates to tvOS is that it’s now compatible with VPNs, although that is clearly designed less for workers and more for consumers who want to watch geo-blocked content.
Updates to Managing Apple Watch, iPhone, and iPad
As you can tell, we’re primarily concerned with WWDC’s news regarding macOS devices. Still, it’s worth briefly touching on Apple’s push to make its other products more enterprise-friendly, if only because it offers an interesting look at the tension between Apple’s commitments to IT and end users.
Return to service debuts for iOS and iPadOS, enabling IT to wipe and reset these devices via MDM. That’ll be a godsend for schools and businesses with high device turnover.
Account-driven device enrollment builds on account-driven User Enrollment, but for organizations that own the devices they give end users. Like the earlier version, it lets users cryptographically separate their work and personal data on a device by using both a personal and work-issued Apple ID. But it also gives IT the ability to remotely wipe and lock devices, so users will want to be careful not to get too attached to their work-issued iPhone, even if it does have their personal information on it.
Device management for watchOS may not be relevant to the majority of companies, but Apple’s language around it marked an interesting departure from their usual focus on user privacy. They mention their desire to help companies “improve productivity, support wellness, and provide additional safety” but don’t really expand on what that might look like.
Granted, the example they give is pretty innocuous: Volvo giving its technicians Apple Watches so they can work hands-free. But given the intimate nature of a device that lives on your wrist and monitors your heart rate, it’s hard not to imagine the ways this could be misused, especially given the current appetite for bossware.
WWDC 2023 Had More Than Meets the IT
This year’s WWDC may be over, but there’s still a lot about it we don’t know–it’s hard to fully understand these technologies are out in the world and encountering messy, human reality.
But one thing is clear: Apple is making a concerted effort to answer the needs of IT teams, and it’ll be fascinating to see how that work pays off.





